Remote and hybrid work are no longer short-term trends — they have become the structural backbone of how modern organizations operate. Today, companies of all sizes rely heavily on distributed teams who need secure access to internal tools and sensitive data from homes, hotels, airports, coworking spaces, and virtually anywhere else work happens.
However, while remote access delivers flexibility and productivity gains, it also introduces a growing layer of responsibility for IT and security teams. The question shifts quickly from “Can employees work from anywhere?” to “How do we ensure every connection is secure, stable, and compliant?”
As the number of remote users grows, so does the potential attack surface. Businesses must ensure that every connection is properly authenticated, every session is protected with strong encryption, and all policies for network access are enforced consistently. At the same time, performance must remain reliable — even when hundreds or thousands of users attempt to connect simultaneously. Without the right infrastructure, VPN slowdowns, misconfigurations, or worse, data breaches, become real risks.
This is why enterprises invest in remote access solutions specifically designed to scale securely. And this brings us to one of the key components of secure high-volume remote access: the VPN concentrator.
What Is a VPN Concentrator?
A VPN concentrator is a dedicated network device that creates, manages, and encrypts a large number of VPN connections simultaneously. It acts as the secure gateway between external users and private internal systems inside your organization.
The simplest comparison:
A VPN server might support a small remote team.
A VPN concentrator supports complete organizations with hundreds or thousands of remote users.
It centralizes:
- User authentication
- Encryption and key management
- Access control policies
- Traffic throughput and performance
Who typically needs one:
| Organization Type | Reason |
| Large enterprises | High remote user demand |
| Finance and banking | Strong compliance and audit requirements |
| Healthcare | Secure remote access to protected medical data |
| Government & defense | Strict data access control |
| Multi-site companies | Hundreds of tunnels between branches |
In short: if downtime or compromise = business disaster, a concentrator is often part of the solution.
How Does a VPN Concentrator Work?
A VPN concentrator sits at the network edge, behind the firewall and before internal applications. When a remote user connects, the device:
- Identity Authentication: The concentrator verifies the user’s identity using enterprise authentication systems such as Active Directory, LDAP, MFA tokens, or client certificates. This ensures that only authorized personnel can gain access.
- Encryption Negotiation: The endpoint and concentrator agree on cryptographic parameters — commonly through IPsec or SSL/TLS — to establish a protected communication tunnel.
- Secure Tunnel Establishment: A VPN tunnel is created, encrypting data in transit and preventing interception or tampering.
- IP Address Assignment and Routing: The concentrator assigns each user a virtual IP address and decides how traffic should flow based on network policies.
- Access Policy Enforcement: User permissions determine what systems, applications, or internal data the session can reach. This maintains the principle of least privilege.
- Ongoing Encryption and Traffic Protection: All inbound and outbound packets are encrypted and decrypted at line speed to maintain confidentiality and integrity.
- Monitoring, Logging, and Compliance Auditing: User activities are tracked for security response, performance optimization, and regulatory reporting.
Key functions include:
| Feature | Value |
| Hardware-accelerated encryption | Strong performance under load |
| Centralized identity control | One place to revoke or restrict |
| High session capacity | Hundreds to thousands of tunnels |
| Resiliency options | Failover clustering to avoid outages |
| Detailed traffic logs | For forensic and compliance audits |
Where a VPN concentrator sits in the network
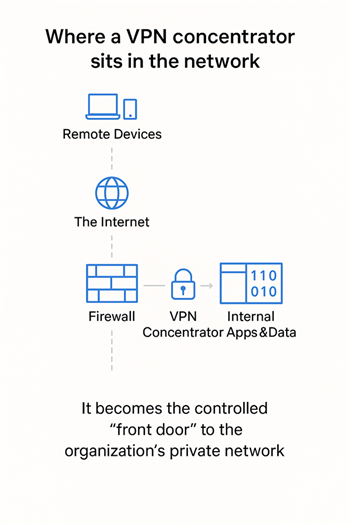
The VPN concentrator is positioned between the organization’s firewall and its internal applications and data. Remote devices connect through the Internet, passing first through the firewall for initial protection. From there, traffic is directed to the VPN concentrator, which authenticates users, establishes secure, encrypted tunnels, and controls access to internal network resources. In this setup, the VPN concentrator effectively serves as the organization’s controlled “front door” — the primary entry point to its private network.
VPN Concentrator vs Other VPN Tools
Because VPN terms often get mixed up, these distinctions help clarify which tool fits which scenario.
1. VPN Concentrator vs VPN Router
| Capability | VPN Router | VPN Concentrator |
| Designed for | Small offices | SMB to large enterprise |
| Session capacity | Dozens | Hundreds to thousands |
| Authentication | Basic | Directory + MFA integration |
| Throughput | Limited | High-performance crypto |
| Cost & management | Low | High |
If you have a small team and mostly SaaS apps, a concentrator is not necessary.
2. VPN Concentrator vs VPN Server / Client
| Component | Function |
| VPN Client | The software on a user’s device |
| VPN Server | Terminates VPN sessions |
| VPN Concentrator | A high-scale VPN server with security management and load handling |
A concentrator is essentially an advanced VPN server optimized for scale.
3. VPN Concentrator vs Site-to-Site VPN
| Question | Site-to-Site | Concentrator |
| Connects individual users? | No | Yes |
| Connects entire networks? | Yes | Yes |
| Best for | Branch linking | Remote workforce |
Both are often deployed simultaneously.
4. VPN Concentrator vs Cloud VPN
| Factor | Hardware Concentrator | Cloud VPN Gateway |
| Deployment | On-prem data center | Fully managed cloud |
| Upfront cost | High | Low |
| Scalability | Limited by hardware | Elastic |
| Maintenance | Internal IT required | Included |
| Security location | Network perimeter | Distributed PoPs |
| Best for | Legacy on-prem environments | Cloud-first remote teams |
This comparison is becoming the core business decision in 2025 and beyond.
Pros and Cons of VPN Concentrators
VPN concentrators play a critical role in securely connecting large numbers of remote users to corporate networks. They offer centralized control and high reliability but also come with cost and scalability considerations. The table below summarizes the key advantages and disadvantages of using VPN concentrators.
| Advantages | Disadvantages |
| Supports high-volume remote access | Hardware + licensing costs add up fast |
| Mature, proven architecture | Requires skilled engineers to deploy and maintain |
| Tight security control from one place | Performance bottlenecks possible if undersized |
| Works well with compliance frameworks | Infrastructure must remain on-premises |
| Reliable when configured with redundancy | Cloud-first businesses may get lower ROI |
They work exceptionally well when needed — but many businesses are buying tech they don’t truly require.
Compliance & Risk Management Benefits of VPN Concentrator
Enterprises often justify concentrators based on auditability and control. They support:
- Role-based access control
- Encryption standards like AES-256 & TLS 1.3
- SIEM integration for real-time alerts
- Full tunnel visibility and logging
- Enforcement of least-privilege access
This makes them strongly aligned with mandates like:
| Compliance Standard | Why Concentrators Help |
| HIPAA | Protect PHI access |
| PCI DSS | Encrypt card data and log access |
| SOC 2 | Demonstrable access controls |
| SOX | Centralized authentication verification |
If your security team lives in spreadsheets and audit logs, a concentrator is often appealing.
Do You Need a VPN Concentrator? (Decision Guide)
Use this quick guide to determine whether a VPN concentrator fits your organization’s needs.
✅ You Probably Do if:
- You support 100+ remote workers daily
- Mission-critical applications are hosted internally
- You must meet government or financial compliance standards
- Users experience frequent VPN slowdowns or disconnects
- You have in-house networking expertise for deployment and maintenance
❌ You Probably Don’t if:
- You have fewer than 50 remote users
- Most of your applications are SaaS or cloud-hosted
- You have no strict audit or compliance requirements
- Your IT staff or budget is limited
Still Unsure? Consider the direction of your infrastructure:
- Expanding your on-prem data center? A concentrator may be a smart investment.
- Migrating toward the cloud? Modern cloud VPN or zero-trust solutions may be a better fit.
3 Modern Alternatives: Cloud VPN and Zero Trust
Traditional hardware-based VPN concentrators are no longer the only option for securing remote access. As businesses move toward hybrid and cloud-first infrastructures, many small and mid-sized organizations are embracing modern, flexible security models that align with their digital transformation goals.
1. Cloud VPN Gateways
Cloud VPN gateways are fully managed by service providers, eliminating the need for physical hardware or complex on-premises setups.
Key advantages include:
- No infrastructure overhead: No hardware to buy, rack, power, or patch.
- Instant scalability: Easily add or remove remote users as demand fluctuates.
- High availability: Redundant, globally distributed infrastructure reduces downtime risks.
- Simplified management: Centralized dashboards streamline configuration and monitoring.
This model is particularly attractive for organizations that want reliable, secure access without expanding their own data center footprint.
2. Zero Trust Network Access (ZTNA)
Zero Trust Network Access represents a significant shift from the traditional “connect-then-trust” VPN model. Instead of granting users broad network access, ZTNA enforces identity-based, per-application access controls.
Core benefits include:
- Granular authentication: Each user and device is verified before accessing a specific app.
- Minimized exposure: Users never see or access parts of the network they don’t need.
- Enhanced security posture: Limits lateral movement in case of account compromise or malware infection.
ZTNA is well-suited for distributed teams and organizations handling sensitive data who want to move beyond perimeter-based security.
3. SASE (Secure Access Service Edge)
SASE combines networking and security into a unified, cloud-delivered platform. It integrates capabilities such as secure web gateways, cloud access security brokers (CASB), and SD-WAN under one architecture.
Key benefits include:
- Unified management: Security and connectivity are managed through a single service.
- Global optimization: Data routes through the nearest point of presence (PoP) for faster performance.
- Ideal for international teams: Ensures consistent, low-latency access regardless of user location.
SASE is particularly advantageous for global enterprises seeking both scalability and consistent policy enforcement across regions.
Why These Cloud Approaches Matter
Cloud-based security aligns naturally with today’s cloud-native infrastructure. As users and applications move off-premises, security must follow them. Adopting solutions like Cloud VPN, ZTNA, or SASE allows organizations to maintain enterprise-grade protection while reducing operational complexity.
Modern providers such as BearVPN exemplify this trend — helping businesses offload the burden of remote access management while ensuring robust, scalable, and compliant security without owning or maintaining hardware.
Popular VPN Concentrator Vendors
Most enterprise evaluators focus on:
- Cisco (Meraki, ASA + AnyConnect)
- Fortinet FortiGate Appliances
- Palo Alto Networks GlobalProtect Hardware
- Juniper Secure Connect
- Aruba VPN Gateways
These products are powerful but require careful planning and skilled operations.
FAQs on VPN Concentrator
- Where should a VPN concentrator be installed?
A VPN Concentrator is typically installed behind the organization’s firewall, positioned at the network perimeter. This setup ensures that all inbound and outbound VPN traffic passes through both the firewall and the concentrator. The firewall handles packet filtering and intrusion prevention, while the VPN Concentrator manages encryption, authentication, and secure tunnel creation.
- Which VPN protocols do VPN Concentrators support?
Commonly IPsec, SSL/TLS, IKEv2, and vendor-specific enhancements.
- Can VPN Concentrators run in the cloud?
Yes. Most major VPN vendors now offer virtual VPN Concentrators that run on leading cloud platforms such as AWS, Microsoft Azure, and Google Cloud Platform (GCP).
- How many users can VPN Concentrators support?
100 to 5,000+ depending on appliance class and cluster configuration.
- Do VPN Concentrators support Multi-Factor Authentication (MFA)?
Yes — often with built-in or integrations like Duo, Okta, and Azure AD.
- Can cloud VPN replace a hardware concentrator?
increasingly yes — especially for cloud-first teams or SMBs.
Conclusion
VPN concentrators remain a reliable choice for organizations with many remote users, on-premises critical systems, and strict compliance needs. They provide strong security and scalability — but also come with higher costs and management demands.
As more businesses move to the cloud, security must adapt to follow users wherever they work. Modern cloud VPN gateways and Zero Trust solutions now offer equal or greater protection with far less operational effort.
If you’re exploring remote access options, BearVPN can help you choose the right fit — whether that’s traditional hardware or a cloud-based secure access model. The best security should protect your business without slowing it down.